VNC
New Olex versions includes VNC, which lets the system be viewed and controlled by other computers, locally or over Internet. You can use your office computer, iPhone, iPad etc to operate and view the full Olex display onboard the boat. For truly remote control, it also lets you call up a terminal window, to type commands into.
VNC is useful for Olex resellers to remotely diagnose and fix Olex systems. It can also be used to give secondary displays onboard a boat. For example, the skipper may use his iPad to monitor Olex from his bunk.
VNC is akin to TeamViewer, but fully free. It does not use TeamViewer's centralized server method, instead VNC server and client communicate directly. TeamViewer at first started as an offshoot from VNC.
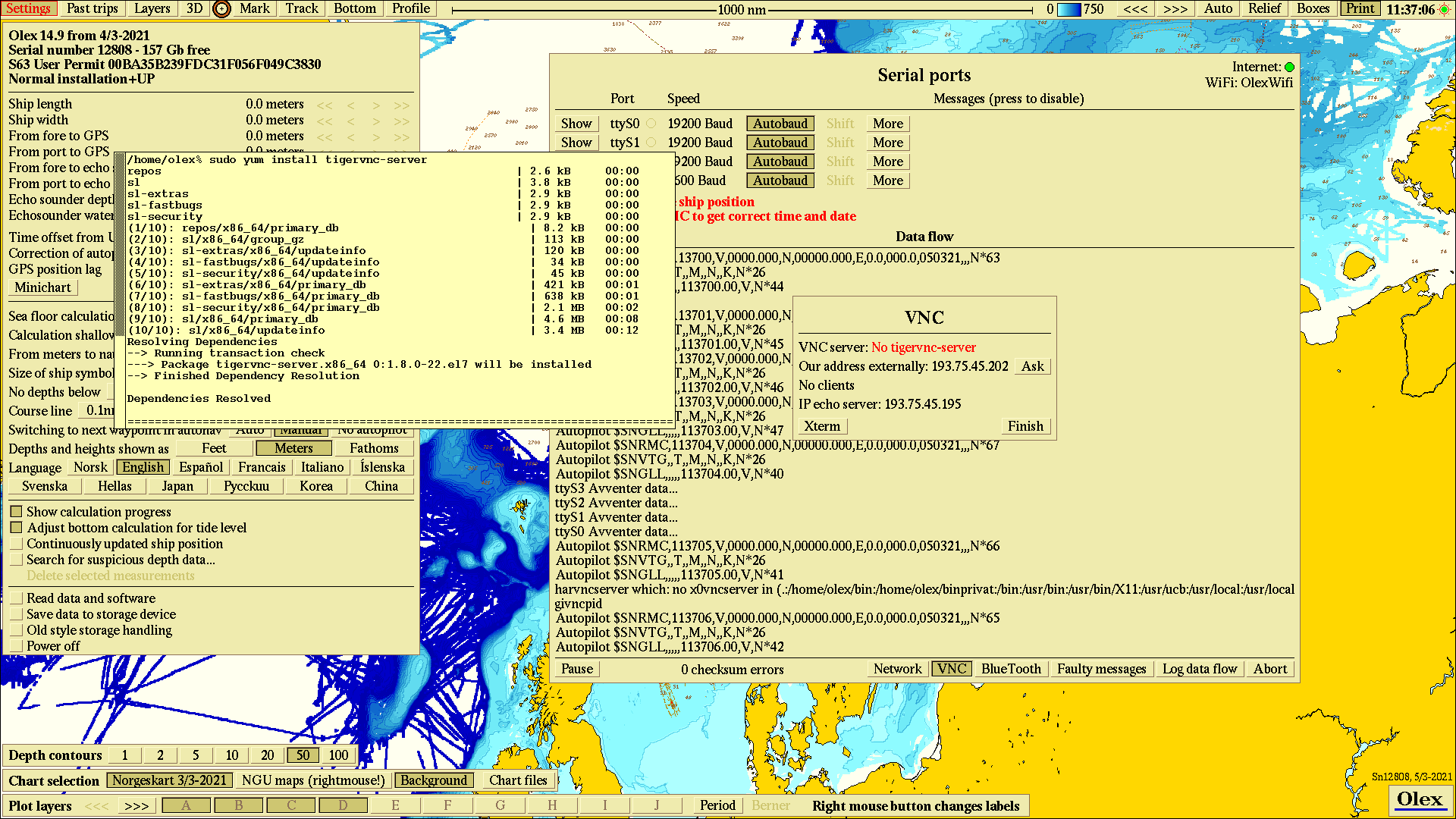
The easiest path to VNC is to reinstall Linux using CentOS 8.3, downloadable from our site, meaning new installs will be ready for VNC from the getgo. Systems that originated prior to March 2021 need an additional component called "tigervnc-server". This software may not be available for old operative systems but should still be available, on the Internet, for Scientific Linux 7.6 or later.
However, for systems running on a computer model M3 or later, a reinstall with CentOS 8.3 will often be the easiest way. This can be arranged through your Olex dealer.
To access Olex over Internet, the router may need reconfiguring. The feature is called "port forwarding", "DMZ", or other buzzwords. It varies greatly between different routers. Google for how to run VNC via Internet.
The issue is that an Olex behind a router is not normally accessible from Internet. Yes you may browse web sites, but no they cannot reach you. The router gives Olex a "local" address, like 192.168.1.152, while outwards the address is something decided by the router and ISP, aka 77.66.189.24. Talking back to this apparent address doesn’t hit Olex, but falls on deaf ears inside the router. But by configuring the router, Olex may be set as the one recipient for external communications.
Skippers should probably not modify their router themselves. Olex resellers might assist with configuring existing routers, or provide dedicated routers preconfigured for VNC.
Intial setup
1) Note what address Olex use to connect through the router. This will typically be the one denoted by WiFi or DHCP on the Olex Network panel.
2) Modify the router by putting this address as its "DMZ", or similar means. The actual name or mechanism surely varies between routers. You may have to scrutinize its manual. The crux of the matter is to inform the router which of its connected devices shall be identified by the routers own Internet address.
3) By any luck the router will assign the same IP adress to Olex upon every startup so that you don’t need to redo 2). Maybe you can tie it to the MAC address instead.
Daily use
4) When the skipper want to let someone run his Olex remotely, he press "Ask" on the VNC pane, found on the Data flow window. This send a simple request to a server, who respond with the address the request came from. The VNC pane will thus show what address this Olex can be reached at. This address will likely vary semi-randomly.5) The skipper informs the other party of this address-to-Olex-from-Internet.
6) The skipper enable VNC by pressing "Start" on the VNC pane. Once the local server is running, part of the top menu line turn green as a warning.
7) The "Start" button may be protected by password, the same as protecting external memory devices. Just as with the devices, the intent is to prevent unauthorized actors from accessing the system. This password is set/modified/cleared on Layers -> Default settings for new data.
8) To kill the VNC link, the skipper press "Stop" on the VNC pane. Buttons and controls turn green throughout Olex to guide the skipper back to this pane, in case he forgets where to find it.
9) The VNC pane details how many clients are currently connected.
10) The remote party use his VNC client to acces the Olex. He types in the address given by the Olex. There are several VNC clients available.
Security
One may be concerned about rogue actors connecting through VNC to spy on secret data or remotely operate the system.
VNC can have several layers of security: the VNC client must give a password before connecting; blacklists may exempt certain machines from connecting; nonstandard port numbers may be used etc.
We have currently chosen not to implement these means, in order to avoid too much complexity. We think the fact that the skipper will only activate VNC when he want to, and that his address is neither static nor easily found, gives a reasonable degree of security. This policy may be changed if so demanded.
